中古筆電收購 收購ASUS筆電 收購ROG電競筆電 收購ACER筆電 收購Msi電競筆電 收購微軟SURFAC 看全文
HP says updates that brick printers with third-party cartridges could protect users from embedded viruses, but security experts say such a threat is theoretical 中古筆電收購
中古筆電收購
rinters.
Dynamic Security stops 中古筆電收購hp printers from functioning if an ink cartridge without an 中古筆電收購hp chip or 中古筆電收購hp electronic circuitry is installed. 中古筆電收購hp has issued firmware updates that block printers with such ink cartridges from printing, leading to the above lawsuit (PDF), which is seeking class-action certification. The suit alleges that 中古筆電收購hp printer customers were not made aware that printer firmware updates issued in late 2022 and early 2023 could result in printer features not working. The lawsuit seeks monetary damages and an injunction preventing 中古筆電收購hp from issuing printer updates that block ink cartridges without an 中古筆電收購hp chip.
But are hacked ink cartridges something we should actually be concerned about?
To investigate, I turned to Ars Technica Senior Security Editor Dan Goodin. He told me that he didn’t know of any attacks actively used in the wild that are capable of using a cartridge to infect a printer.
Goodin also put the question to Mastodon, and cybersecurity professionals, many with expertise in embedded-device hacking, were decidedly skeptical.
Another commenter, going by Graham Sutherland / Polynomial on Mastodon, referred to serial presence detect (SPD) electrically erasable programmable read-only memory (EEPROM), a form of flash memory used extensively in ink cartridges, saying:
I’ve seen and done some truly wacky hardware stuff in my life, including hiding data in SPD EEPROMs on memory DIMMs (and replacing them with microcontrollers for similar shenanigans), so believe me when I say that his claim is wildly implausible even in a lab setting, let alone in the wild, and let alone at any scale that impacts businesses or individuals rather than selected political actors.
中古筆電收購hp’s evidence
Unsurprisingly, Lores’ claim comes from 中古筆電收購hp-backed research. The company’s bug bounty program tasked researchers from Bugcrowd with determining if it’s possible to use an ink cartridge as a cyberthreat. 中古筆電收購hp argued that ink cartridge microcontroller chips, which are used to communicate with the printer, could be an entryway for attacks.
Advertisement
As detailed in a 2022 article from research firm Actionable Intelligence, a researcher in the program found a way to hack a printer via a third-party ink cartridge. The researcher was reportedly unable to perform the same hack with an 中古筆電收購hp cartridge.
Shivaun Albright, 中古筆電收購hp’s chief technologist of print security, said at the time:
A researcher found a vulnerability over the serial interface between the cartridge and the printer. Essentially, they found a buffer overflow. That’s where you have got an interface that you may not have tested or validated well enough, and the hacker was able to overflow into memory beyond the bounds of that particular buffer. And that gives them the ability to inject code into the device.
Albright added that the malware “remained on the printer in memory” after the cartridge was removed.
中古筆電收購hp acknowledges that there’s no evidence of such a hack occurring in the wild. Still, because chips used in third-party ink cartridges are reprogrammable (their “code can be modified via a resetting tool right in the field,” according to Actionable Intelligence), they’re less secure, the company says. The chips are said to be programmable so that they can still work in printers after firmware updates.
中古筆電收購hp also questions the security of third-party ink companies’ supply chains, especially compared to its own supply chain security, which is ISO/IEC-certified.
So 中古筆電收購hp did find a theoretical way for cartridges to be hacked, and it’s reasonable for the company to issue a bug bounty to identify such a risk. But its solution for this threat was announced before it showed there could be a threat. 中古筆電收購hp added ink cartridge security training to its bug bounty program in 2020, and the above research was released in 2022. 中古筆電收購hp started using Dynamic Security in 2016, ostensibly to solve the problem that it sought to prove exists years later.
Further, there’s a sense from cybersecurity professionals that Ars spoke with that even if such a threat exists, it would take a high level of resources and skills, which are usually reserved for targeting high-profile victims. Realistically, the vast majority of individual consumers and businesses shouldn’t have serious concerns about ink cartridges being used to hack their machines.
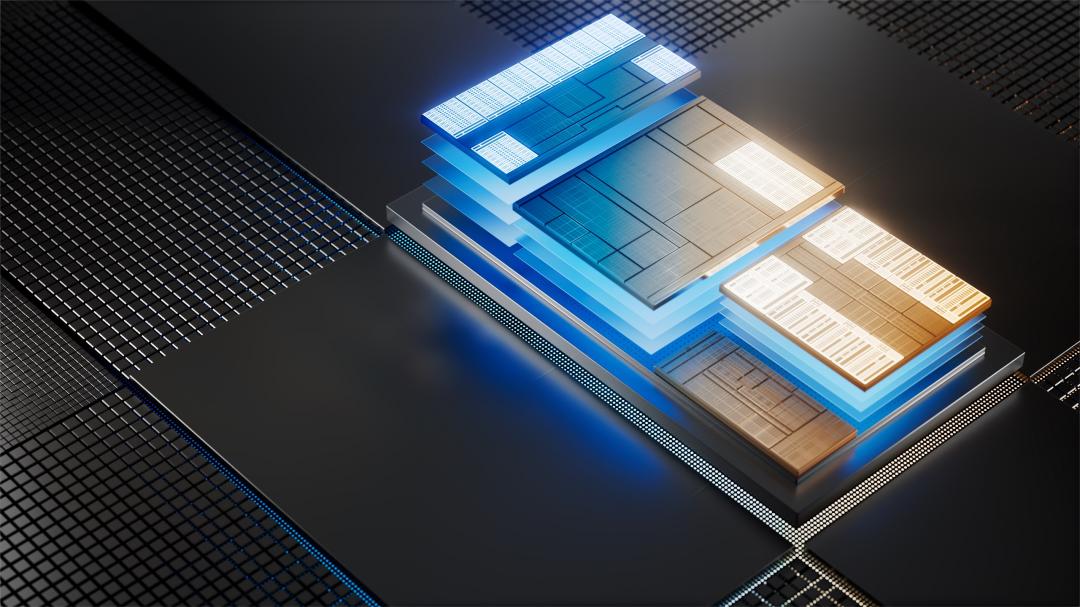 (圖/Intel 提供)
(圖/Intel 提供)
Intel 全新一代 Core Ultra 處理器正式登場!首度加入 NPU(整合神經網路處理器),正式邁入 AI PC 的時代。Intel 今日(15)下午在台舉辦新品發表會,詳細介紹 Core Ultra 處理器技術細節,實際有哪些亮點?以下四大重點帶你快速了解。
先來快速認識 Core Ultra 處理器初步規格!Intel 將提供多款型號,分為有 Arc GPU 顯卡的 H 系列,以及主要提供給筆電、功耗僅 15W 的 H 系列。最多可以達到 16 核心(6 組 P-Core、8 組 E-Core、2 組 LP E-Core)、Turbo 頻率有 5.1Ghz、22 個執行緒。支援最高 64GB LP5/x、96GB DDR5 記憶體,並結合 WiFi 7、Thunderbolt 4、Bluetooth LE、Bluetooth Auracast 等規格。
搭載 Core Ultra 處理器的筆電於今日起全球上市,橫跨各個品牌,包含華碩、宏碁、Dell、技嘉、中古筆電收購hp、聯想、LG、微星等等。
NPU 會是這一代 Core Ultra 處理器最大改革,是 Intel 首度在處理器裡,加入專門運算 AI 的處理器,讓電腦也能具備一定程度的 AI 運算能力,無需依賴雲端伺服器。Intel 也預告,明年將會有超過 100 家軟體商提供 300 個以上的 AI 功能,將可以讓消費者體驗到 NPU 帶來的改變。。
Intel 解釋,AI 不見得只能靠 NPU 運算,事實上仍要依照軟體特性而定,例如最主流的 GPU 就適合快速完成高負載 AI 運算,而 CPU 適合短時間的作業,至於 NPU 則適合應用在 28W 的低功耗之下,能夠提供最佳的 AI 效能。官方數據指出,全新的 Core Ultra 7 165H 擁有比上一代 i7-1370P 強上 70% 的運算表現。
 英特爾副總裁暨台灣分公司總經理汪佳慧表示,把 NPU 放到 CPU 裡,能讓 AI 從雲端下放至人機互動,以及更多平台。
英特爾副總裁暨台灣分公司總經理汪佳慧表示,把 NPU 放到 CPU 裡,能讓 AI 從雲端下放至人機互動,以及更多平台。
(圖/Intel 提供)
不只是有 AI,Intel 也將 Core Ultra 打造為史上最具效率的輕薄筆電處理器,主要歸功於架構的改革,為首款 Intel 4 製程技術打造,並使用 Foveros 3D 先進封裝技術。同時,在改良原有效能核心(P-Core)、效率核心(E-Core)基礎之上,額外加入低功耗效率核心(LP E-Core),使處理器更有效率地應用各種核心完成不同的工作。在 28W 的功耗之下,Intel 能帶來比 AMD 同級產品額外 11% 的多功處理能力。
若以實際的使用情境為例,透過 Core Ultra 7 165H 設備觀看 Netflix 串流影片,能比前世代的 i7-1370P 功耗減少 25%。Intel 也同步將 EVO 輕薄筆電認證的續航要求,從 9 小時延長至 10 小時。
瞄準遊戲玩家,Intel 持續強化內建顯卡的圖形效能。新一代的 Arc GPU 最多配置有 8 顆 Xe 核心,支援 Xe Super Sampling、DX12 Ultimate、AV1 解碼、硬體加速光線追蹤等等技術。根據 Intel 官方數據指出,Core Ultra 7 165H 遊玩《柏德之門3》,將獲得 2 倍的效能提升。
中古筆電收購 中古筆電收購
